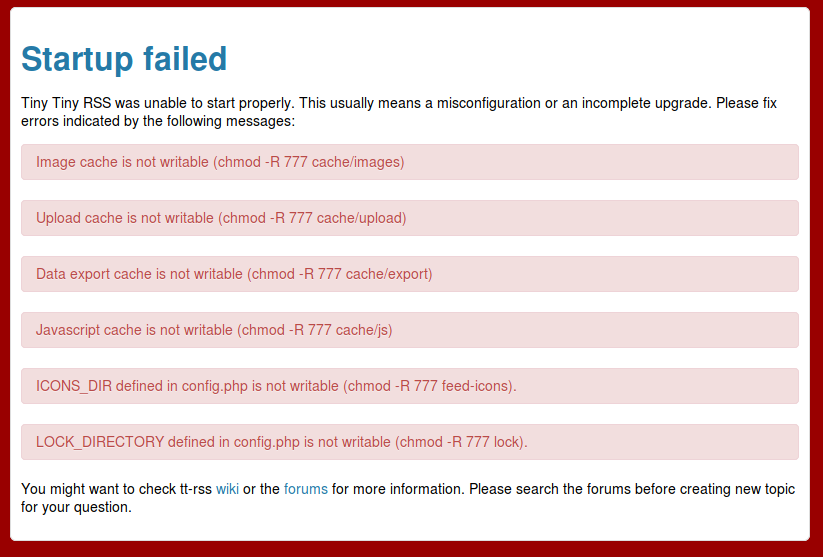
Hello there.
I’ve made this acc just for you, because I find this topic amusing. You type like English isn’t your first language, so I’ll keep it simple. I have the feeling that you don’t know that much about security and just read that 777 is a no-no in some forum.
If someone were to exploit the server, it doesn’t matter what permissions the file has.
To run a server, there has to be a user with permissions to, well, run the server.
Whichever user that is, is going to be who the attacker is going to get a shell as.
www-data is a standard underprivileged user designated to run web services.
The files in question need to be read/write/execute so that www-data can run the server.
As conrad said, you don’t need to have them be 777, you can just have their owner be www-data and have www-data be the only person who can read/write/execute them.
Again however, this doesn’t matter, because if you’re running a web server, the attacker’s going to be www-data if he gets in through the web server.
The only reason to be anal about the permissions of files on the web server is if there are regular users who you don’t trust that connect to your machine for some reason, in which case the solution would be to not permit random users to access the machine hosting the web server.
Only the administrator of the server should be allowed to modify things on the box. Do not, and I repeat, do not, use a machine that hosts live, internet-facing services for anything other than hosting those services unless you really know what you’re doing.
If you actually want a reasonable degree of web server security, the far better thing would be to set up docker and run the web server in an instance of it, or chroot jail.
If I were you I’d read a bit more about the topic, having a public facing web server is dangerous if you don’t know how stuff works.
EDIT: The permissions not mattering is just for this case. Do make sure to properly set permissions in multi-user environments, especially to restrict access to sensitive files.